Imagine waking up to dozens of customer complaints. Your store’s sending spam. You can’t log into wp-admin. A new admin account named “AnonymousFox_xyz” has hijacked your site – and maybe even your entire server.
If that sounds familiar, you’re not alone.
Since 2019, the AnonymousFox hack has been quietly (and viciously) targeting WordPress and WooCommerce sites. It’s not just a “technical problem”. It’s lost orders. It’s panic. It’s your business on the line.
If you’ve been hit or just want to stay one step ahead, this article breaks it all down. In plain English. We’ll walk you through:
- What AnonymousFox actually is
- How to tell if your site’s infected
- What to do (step by step)
- And how to make damn sure it doesn’t happen again
Let’s kill the panic and take back control.
What Is the AnonymousFox Hack (and Why WooCommerce Sites Should Care?)
AnonymousFox is a sophisticated, evolving hacking toolkit used by cybercriminals to hijack mostly WordPress and WooCommerce websites. It scans for weak points (outdated plugins, misconfigured servers, exposed credentials), slips in, and then takes over – fast.
Once inside, it does more than just create a new admin account. It can:
- Reset your cPanel password and lock you out
- Replace core files and .htaccess rules to break functionality
- Send thousands of spam or phishing emails from your domain
- Host scam pages on your server
- Damage your SEO or get your domain blacklisted by Google
WooCommerce stores are desirable targets. Why? Because they often run many plugins, store customer data, and downtime means lost revenue – exactly the kind of pressure hackers need.

To make things worse, AnonymousFox has gone through multiple evolutions and aliases (like “Fox Cyber Security”), and it’s still very active today.
Bottom line: if you run a WooCommerce store, this isn’t just a WordPress issue. It’s a direct threat to your reputation, sales, and customers’ trust.
How to Tell If AnonymousFox Has Hacked Your Store?
Not every site with weird behavior is infected with AnonymousFox – but if you see one or more of these “red flags”, it’s time to act fast. This checklist tells you where to inspect for suspicions:
- You’re Locked Out of wp-admin
Suddenly can’t log in? Password reset emails not arriving? The fox may have changed your admin email or password and locked you out completely.
- Suspicious New Admin Accounts
Look for user accounts you didn’t create – especially with names like:
- Anonymousfox_xyz
- admin@fbi.gov (yes, really…)
- Random strings like sys_adm_998
If you’re still logged in, go to Users → All Users and scan for unfamiliar names with admin control.
- Unknown Plugins or Files
Check for shady plugins you didn’t install, such as:
- fox-ccfs
- wpyii2
- plugin::Fox
Also check /wp-content/uploads/ for strange PHP files (e.g. rgyyu.php, mail_send.php) and subfolders that weren’t there before.
- Your Email or Domain Is Sending Spam
If your customers report weird emails “from you,” or your host flags outgoing email issues, chances are your site has been turned into a spam cannon.

You can also check this yourself:
- Look for SMTP activity in your host’s email logs
- Use tools like MXToolbox to see if it’s blacklisted
- Your Contact Email Was Changed
In your hosting panel or WordPress settings, check if the main contact email has been changed, because hackers often change this to intercept password resets.
- Your Site Loads Spam or “Japanese words”
Some site owners have found Japanese spam posts, pharmaceutical pages, or strange redirects on their store.
Google may even mark your site as “This site may be hacked.”
Pro tip:
Check Google Search Console → Pages → Crawled → Last 30 days to spot unauthorized content.
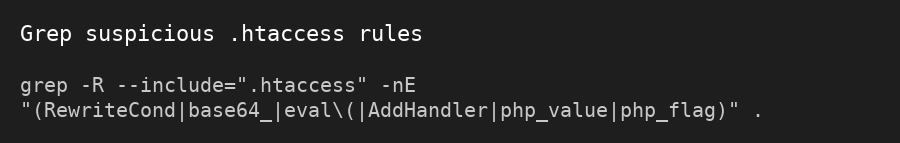
- Strange .htaccess or php.ini Files
If your host or developer finds a bunch of .htaccess or php.ini files throughout your folders (especially with weird deny/allow rules), that’s a classic AnonymousFox tactic to block your admin access or disable security.
- Site is Sluggish or Broken
If orders are failing, checkout is freezing, or admin buttons don’t work – you might be dealing with sabotaged file permissions or intentional breakage.
If you spot even one major red flag, don’t ignore it. AnonymousFox spreads fast – and the longer it sits, the more it damages. In the next section, we’ll show you exactly how to clean it up.
Steps to Remove the AnonymousFox Malware from Your WooCommerce
If you find “the fox”, don’t panic – but don’t waste time either.
This is your step-by-step action plan. Whether you’re doing this yourself or handing it to a developer, follow each part carefully. Skip one, and hackers might sneak back in.
Step 1: Quarantine Your Site & Back It Up
Before you touch anything, temporarily put your site in maintenance mode (via plugin or cPanel) and ask your host to suspend outgoing email (if spam is being sent).
Make a full backup (files + database), even if it’s infected (better to have a copy than lose everything).
Step 2: Regain Access to Your Admin
If you’re locked out of WordPress:
- Log in to your cPanel → phpMyAdmin
- Find the wp_users table
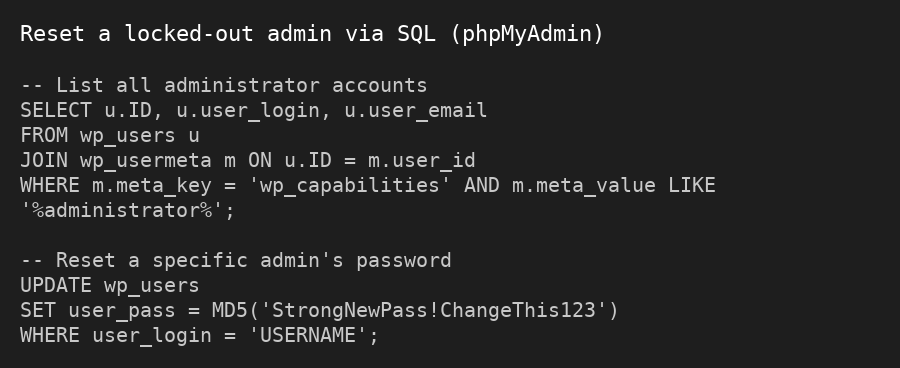
If your tables use a different prefix (e.g.,
abcd_), replace wp_ accordingly.- Locate your admin account and:
- Reset the password (use this guide from WordPress)
- If your username/email was changed, fix it too
Next:
- Check the wp_users table for unknown admin users and delete them
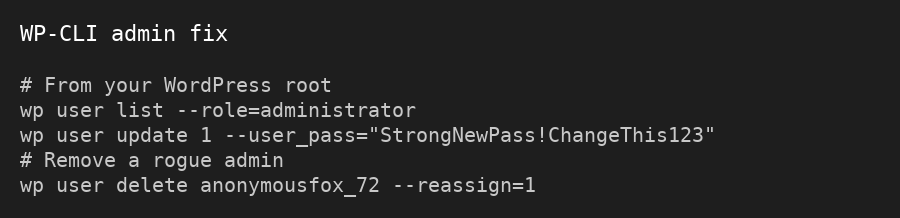
- Update your database password (optional but smart), and update it in wp-config.php
Step 3: Remove Malware Files & Backdoors
Now the real cleanup begins.
Install a plugin like MalCare or Wordfence to scan and auto-remove known threats. These tools won’t catch everything, but they’ll handle the obvious junk.
Then, manually delete anything suspicious in:
- /wp-content/plugins/ → Look for anything “fox”, random, or recently modified
- /uploads/ → Check for PHP files (shouldn’t be there) or weird folders
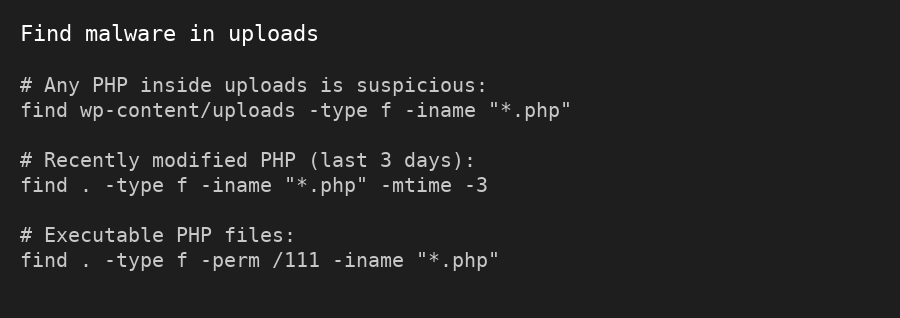
- Root & wp-admin folders → Look for odd .htaccess, php.ini, or unknown .php files
- Compare core files to a clean version of WordPress. Replace anything that’s been changed (like index.php, wp-blog-header.php, etc.)

After that, check wp_posts for hidden spammy posts and look for hidden cron jobs or injected scripts in settings.
Step 4: Clean Up Your Server (cPanel)
This part most tutorials skip – and it’s where AnonymousFox often hides.
- Reset your cPanel password
- Go to Email Accounts: delete anything the hacker added (look for names like “smtpfox”)
- Check for shady FTP accounts, cron jobs, and forwarders
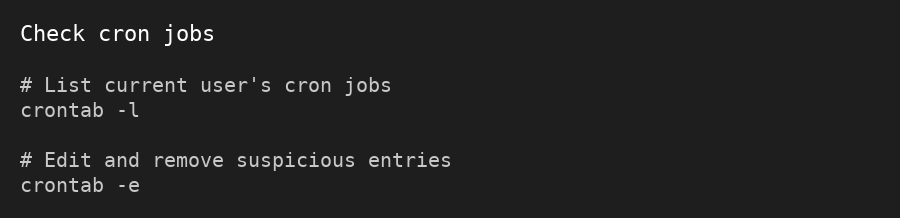
/uploads/ or unknown paths.- If your hosting account has multiple sites, scan them all. One infected site can reinfect the others
Step 5: Update & Harden Everything
In the end, update WordPress core, all plugins, and themes. Delete unused plugins/themes completely.
Review your plugin list for anything unnecessary or risky (especially file managers).
Now’s the time to install Two-Factor Authentication for all admin users. You can use a plugin like WP 2FA or miniOrange.
Feeling Overwhelmed?
Cleaning up a deep, server-level hack isn’t your typical “click and fix” WordPress problem. It’s technical, time-sensitive, and easy to mess up if you’re not used to digging through databases and hidden malware files.
If you’re unsure or just want it done fast and right, you can consider professional help – but if you’re eager to do it on your own, you’ll need some knowledge of WordPress, servers, and PHP.
How to Prevent the AnonymousFox Hack in the Future

AnonymousFox evolves constantly, so your best defense is building solid habits and closing every door it might sneak through:
- Keep everything updated
WordPress core, plugins, themes, even your PHP version – outdated software is the #1 entry point for AnonymousFox. Set a weekly update schedule and stick to it.
- Delete unused plugins and themes
If it’s not essential, remove it. Inactive tools still run code, and hackers know it.
- Use a firewall or security plugin
Tools like MalCare or Wordfence do more than scan – they block brute-force logins, flag suspicious changes, and stop known exploits in real time.
- Harden your WordPress install
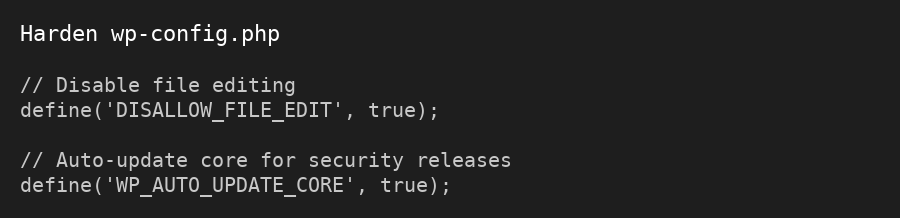
Add small but powerful tweaks:
- Disable file editing in wp-admin
- Limit login attempts
- Change the default login URL
- Use unique database table prefixes
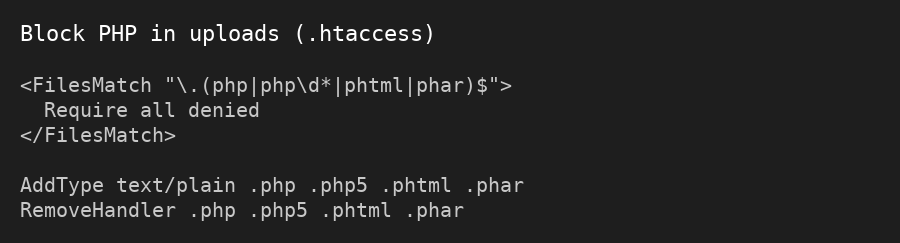
/uploads with a local .htaccess- Automate backups and scans
Set up daily backups and weekly full-site malware scans. If something breaks, you’ll want a clean fallback.
- Secure your hosting environment
Reset cPanel and FTP passwords regularly, review account access, and ask your host to help monitor for unusual behavior.
For this purpose and to make things easier, we made a Security Checklist to keep you safe from AnonymousFox Hack – you can download it, it’s completely free.
How We Helped a Custom Auto Parts Store Recover from This Hack

A client who wants to remain anonymous (same as the fox XD) noticed something odd about his WooCommerce store selling high-performance auto parts.
His customers were receiving invoice emails for products they never ordered, all sent from his domain. But inside WooCommerce, there were no matching orders.
Stranger still, the emails contained exact part numbers from his store, suggesting someone had access to his product database.
Customers reported phishing emails that looked like order confirmations – but linked to scam sites. At the same time, the owner found himself locked out of wp-admin. A new user with “not so unique name” anonymousfox_72 had appeared, and password reset emails stopped arriving.
That’s when he called us.
We investigated and confirmed:
- AnonymousFox had injected mailer scripts into the /uploads/ directory, using his product data to craft convincing fake invoices
- The attacker modified .htaccess files to block admin logins and deny access to malware scanners
- The entire /wp-content/themes/ folder had duplicated shells disguised as theme files
We:
- Recovered wp-admin access via phpMyAdmin
- Cleaned over 180 injected files, including hidden cron jobs and fake “theme” folders
- Removed rogue cPanel email accounts and reset server credentials
- Rebuilt the email sending stack and restored domain reputation
- Set up firewall rules, plugin monitoring, and a secure backup routine
His biggest relief was that transactional emails are now secure, and customers never saw another fake invoice again.
Within 36 hours, his store was operational and now runs with tighter security than ever.
Want to Never Worry About This Again?
If reading all this felt overwhelming, imagine dealing with it at 3 AM – while orders are stuck, customers are angry, and your site is sending spam behind your back.
The truth is, hacks like AnonymousFox aren’t going away. They’re getting smarter, sneakier, and faster at exploiting even the smallest gaps.
That’s why the smartest decision is choosing proactive protection over panic mode.
Our Ecommerce Maintenance Service isn’t just about fixing problems after they happen. We help prevent them in the first place:
- Regular updates for WordPress core, plugins, and themes
- 24/7 uptime and malware monitoring
- Daily off-site backups
- Security hardening tailored for ecommerce
- Fast cleanup and support if anything slips through
We’ve already helped stores recover from AnonymousFox attacks and come back stronger.
Let us handle the foxes, so you can focus on business.





